Mastering Kali Linux: A Comprehensive Guide to Ethical Hacking and Penetration Testing
- Modules : 10
- Duration: 40 Hours
- Level : Expert
- Rating : ★★★★★
Popular Linux distribution Kali Linux was created especially for penetration testing and digital forensics. Numerous penetration testing tools that are used for network discovery, vulnerability assessment, exploitation, and security auditing are pre-installed on it.
There are several online and in-person courses that may assist you in achieving your objectives if you’re interested in studying Kali Linux and how to use its tools for security reasons. These classes cover a variety of topics related to Kali Linux and its tools and vary in difficulty from beginner to expert.
Description:
Are you excited to learn more about ethical hacking and cybersecurity? You need look no further than our in-depth course on learning Kali Linux. This course offers a deep dive into the potent tools and methods necessary for carrying out efficient penetration tests and safeguarding digital environments, and is tailored for both novices and seasoned experts.
What you will discover:
Introduction to Kali Linux: Overview of Kali Linux Learn about the characteristics, function, and importance of the Kali Linux operating system in the field of cybersecurity.
Linux Fundamentals: Learn the fundamentals of Linux command-line operations, file system navigation, user administration, and shell programming.
Networking Fundamentals: Acquire knowledge of core networking topics, such as network protocols, TCP/IP principles, and network reconnaissance methods.
Penetration Testing Methodologies: Examine the stages involved in a penetration test, such as reporting, post-exploitation, exploitation, scanning, and reconnaissance.
Exploitation Techniques: Learn how to employ a variety of exploitation tools and methods, including as SQL injection, cross-site scripting (XSS), privilege escalation, and Metasploit.
Wireless Security: Recognize the weaknesses in wireless networks and find out how to use programs like Aircrack-ng and Wireshark to do wireless penetration tests.
online Application Security: Learn about common vulnerabilities in online applications and how to use tools like OWASP ZAP and Burp Suite to find and attack them.
Forensic Analysis: Discover the fundamentals of digital forensics, including gathering, preserving, analyzing, and reporting evidence.
Course Title: Ethical Hacking and Penetration Testing: A Comprehensive Guide to Mastering Kali Linux
Module 1: Overview of Kali Linux
- Introduction to Kali Linux
- Installation and configuration
- Basic command-line use in Linux
- Overview of the Kali Linux toolkit
Module 2: Understanding Linux
- Shell scripting fundamentals
- File system navigation
- File and directory administration
- User and group management
Module 3: Elements of Networking
- The basics of TCP/IP
- Network protocols (DNS, DHCP, HTTP, etc.)
- Techniques for network reconnaissance
- Network scanning with Nmap
Module 4: Methodologies for Penetration Testing
- An overview of penetration
- Testing Data collection and reconnaissance
- Evaluation of vulnerabilities
- Methods of exploitation
- After-exploitation and preserving entry
- Presenting results
Module 5: Tactics of Exploitation
- Overview of the Metasploit framework
- Using Metasploit to exploit vulnerabilities
- SQL injection attacks
- Attacks using cross-site scripting (XSS)
- Strategies for raising privileges
Module 6: Wireless Security
- Basics of wireless networks
- Wireless Security Protocols
- Using Aircrack-ng for wireless penetration testing
- Analyzing packets with Wireshark
Module 7: Web Application Security
- Overview of web application security
- Recognizing typical online vulnerabilities
- Using Burp Suite to take advantage of web vulnerabilities
- OWASP ZAP for web application scanning
Module 8: Forensic Analysis
- An overview of digital forensics
- The gathering and storage of evidence
- Methods for forensic analysis
- Reporting on forensic discoveries
Module 9: Advanced Topics
- Sophisticated methods of exploitation
- Attacks using social engineering
- Fundamentals of cryptography
- Protecting against frequent assaults
Module 10: Capstone Project
Utilize the information and abilities you’ve learned throughout the course to complete a practical capstone project. Examples of these projects include carrying out forensic investigation on a compromised system or running a penetration test on a fictitious network environment.
Additional Resources:
Online resources, community forums, and suggested reading lists for advancing knowledge and abilities.
This program covers the fundamental ideas and methods of penetration testing, ethical hacking, and Kali Linux in an organized manner, moving from basic to advanced subjects. To support learning goals, each module provides theoretical justifications, real-world examples, and interactive tasks.
Indeed, networking is the broad term for the process of integrating computers and other devices in order to exchange data and resources. It makes it possible for various devices to communicate
Popular Linux distribution Kali Linux was created especially for penetration testing and digital forensics. Numerous penetration testing tools that are used for network discovery, vulnerability assessment,
The phrase “Python for Hackers” describes the use of the Python programming language to penetration testing, cybersecurity, and hacking. Because of its ease of use, adaptability, and many modules
Of course! The goal of an ethical hacking course is to educate students how to evaluate the security posture of computer networks, applications, and systems in a morally and legally compliant manner.
Often called “ethical hacking,” network penetration testing is the process of mimicking cyberattacks on a network infrastructure in order to find holes and flaws. The objective is to evaluate the network’s
Active Directory penetration testing is typically conducted by experienced cybersecurity professionals using a combination of manual techniques and automated tools.
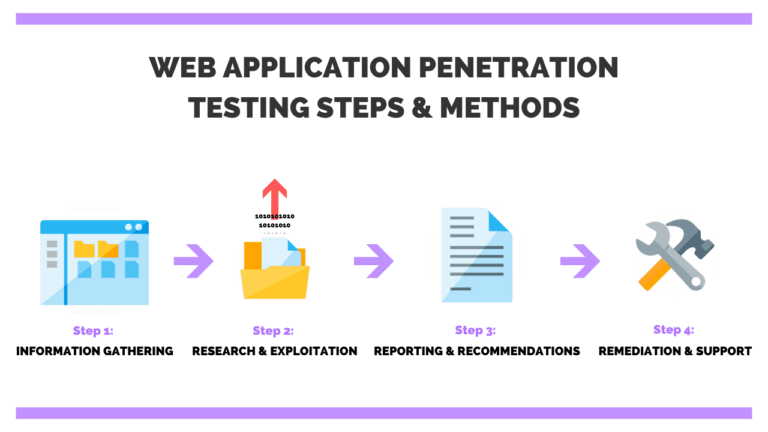
A web application pentesting course often teaches students how to evaluate the security of online applications for possible flaws and vulnerabilities. This sort of training is useful for security experts,
API Pentesting, also known as Application Programming Interface Pentesting, is the process of examining the security of APIs (Application Programming Interfaces) in order to find and eliminate
Mobile application pentesting, also known as mobile app security testing, is the process of assessing the security posture of mobile applications to identify vulnerabilities and weaknesses that could be exploited by attackers.
Frequently Asked Questions
Kali Linux is a specialized Linux distribution primarily used for penetration testing and digital forensics. It comes pre-installed with a wide array of tools used by cybersecurity professionals for tasks such as network analysis, vulnerability assessment, exploitation, and forensic investigations. It’s valuable for identifying and addressing security vulnerabilities in systems and networks.
Kali Linux offers a comprehensive suite of tools for various cybersecurity tasks, including Metasploit for penetration testing, Wireshark for network analysis, Nmap for port scanning, John the Ripper for password cracking, and many others. These tools provide professionals with the capability to assess and improve the security posture of systems and networks.
Individuals proficient in Kali Linux can pursue careers as penetration testers, ethical hackers, security analysts, forensic investigators, security consultants, or security researchers. They can work in various sectors, including government agencies, cybersecurity firms, financial institutions, and technology companies.
Learning Kali Linux can be challenging for beginners due to its advanced nature, but numerous resources are available to help individuals get started. These include online tutorials, documentation provided by the Kali Linux community, video courses, and hands-on labs. With dedication and practice, beginners can gradually build their proficiency in using Kali Linux for cybersecurity purposes.
The average salary for cybersecurity professionals with expertise in Kali Linux in India varies depending on factors such as experience, skills, location, and the employing organization. However, professionals with such expertise can typically expect competitive salaries, ranging from INR 6 lakh to INR 20 lakh per annum or more, depending on their proficiency and role.
The placement prospects for individuals with Kali Linux skills in the cybersecurity industry are generally promising. With the increasing demand for cybersecurity professionals globally, especially those proficient in penetration testing and digital forensics, individuals with Kali Linux skills often find ample job opportunities across various organizations and sectors.
Kali Linux plays a crucial role in enhancing cybersecurity practices and defenses for organizations by providing professionals with a powerful platform to assess, identify, and address security vulnerabilities. Its extensive toolkit allows for thorough penetration testing, vulnerability assessment, and forensic analysis, enabling organizations to proactively strengthen their security posture and mitigate potential threats. Thus, Kali Linux serves as an invaluable asset in safeguarding organizations against cyber threats and attacks.