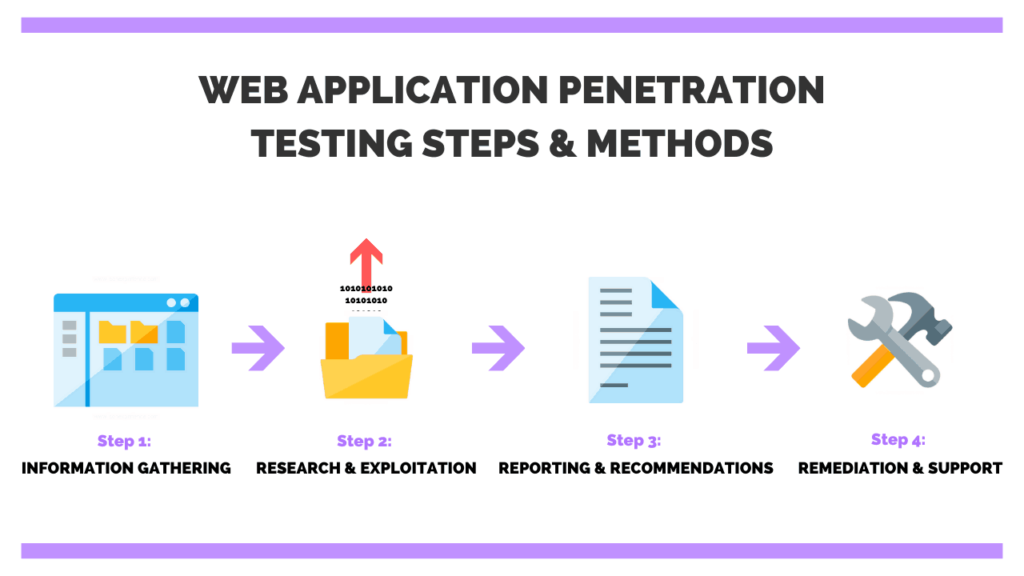
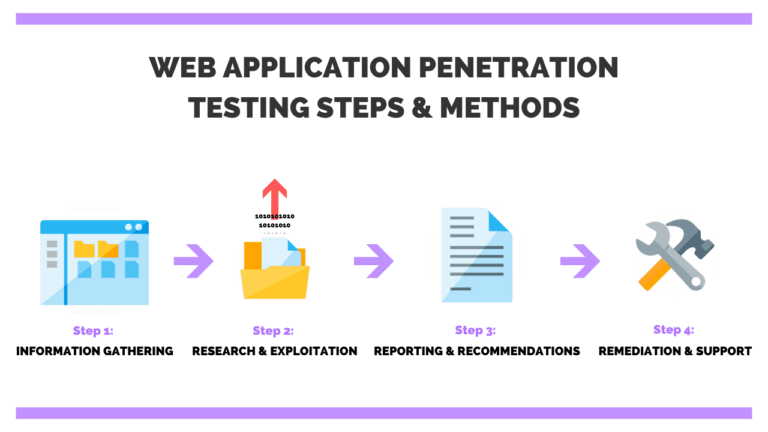
A web application pentesting course often teaches students how to evaluate the security of online applications for possible flaws and vulnerabilities. This sort of training is useful for security experts, developers, and anybody interested in learning how to protect online applications from cyber attacks.
Mastering Web Application Pentesting: Securing the Digital Frontier.
Course Overview:
In the digital age, web apps are the foundation of many organizations and services, but they are also excellent targets for bad actors looking to exploit weaknesses. This thorough course is designed to provide you with the information, tools, and hands-on experience required to properly analyze and protect online applications. Whether you’re a cybersecurity enthusiast, developer, or IT professional, this course will teach you how to discover, exploit, and fix security flaws, therefore protecting key digital assets from possible attackers.
Foundations of Web Application Security:
- Learn the foundations of web application security.
- Investigate typical vulnerabilities and attack paths.
- An overview of essential web technologies and protocols.
Exploring Vulnerabilities:
- Discover common vulnerabilities such as SQL injection and Cross-Site Scripting.
- Practical exercises on identifying and exploiting vulnerabilities using industry-standard technologies.
Advanced Techniques and Tools:
- Using penetration testing frameworks like Burp Suite and OWASP ZAP.
- Exploring sophisticated exploitation and evasion strategies.
- Introduction to automated scanning and manual testing methods.
Real-world Application and Case Studies:
- Analyzing online application breaches and security occurrences.
- Case studies from diverse sectors demonstrate vulnerabilities and their consequences.
Reporting and Remediation:
- Create thorough pentest reports to properly discuss findings.
- Prioritizing vulnerabilities according to risk and possible effect.
- Implementing mitigation measures and best practices to ensure secure development.
Legal and ethical considerations:
- Understanding the legal and ethical ramifications of pen testing.
- Comply with all applicable laws, regulations, and ethical hacking norms.
- Making responsible disclosures and interacting with stakeholders.
Certainly! Here’s an example curriculum plan for a web application pentesting course:
Course Title: Web Application Pentesting Mastery.
Course Duration: 12 Weeks
Week 1: Introduction to Web Application Security
- Understand the significance of online application security
- Explore typical web vulnerabilities and attack vectors
- Learn about the OWASP Top 10 vulnerabilities.
Week 2: Web Technology and Protocols
- Understanding the HTTP/HTTPS protocols.
- Overview of client-side technologies (HTML, CSS, and JavaScript).
- Introduction to server-side technologies (PHP, Python, and Node.js).
Week 3: Web Application Architecture
- Understanding web application components (front-end, back-end, and database).
- An overview of web servers (Apache, Nginx) and databases (MySQL, PostgreSQL).
Week 4: Web App Reconnaissance
- Gathering information and footprints
- Identifying web application access points and attack surfaces.
- Introduction to reconnaissance tools (Nmap, Recon-ng, and Whois).
Week 5: Exploitation Techniques, Part 1
- SQL Injection (SQLi) Attacks and Defenses
- Cross-Site Scripting (XSS): attacks and countermeasures
- Command injection and remote code execution (RCE)
Week 6: Exploitation Techniques, Part 2
- Cross-Site Request Forgery (CSRF) attacks and countermeasures.
- Authentication and session management vulnerabilities
- Directory traversal and file inclusion vulnerabilities
Week 7: Tools for Web Application Pentesting
- Introduction to Burp Suite’s features
- Using OWASP ZAP for automated and manual testing.
- Overview of additional tools (Metasploit, sqlmap, and Nikto).
Week 8: Advance Exploitation and Post-Exploitation
- Exploiting flaws to get unauthorised access.
- Privilege Escalation Techniques
- Data exfiltration and retaining access
Week 9: Reporting and Remediation
- Writing detailed pentest reports
- Prioritizing vulnerabilities according to risk and effect
- Implementing remedial techniques and safe coding practices
Week 10: Legal and ethical considerations.
- Understanding the legal frameworks and compliance standards.
- Ethical Hacking Guidelines and Responsible Disclosure
Engaging with stakeholders and working with development teams
Week 11: Real-World Applications and Case Studies.
- Analyze real-world web application breaches and security issues.
- Case studies from diverse industries (e-commerce, banking, healthcare) provide insights and best practices for preventing similar assaults.
Week 12 – Capstone Project and Certification
- Applying information and abilities acquired during the course.
- Performing a hands-on pentesting project on a given online application.
- Evaluation and certification of complete completion.
This program takes an organized approach to teaching web application pentesting, including key concepts, methodologies, tools, and legal issues. The course approach combines theoretical principles, hands-on laboratories, practical exercises, and real-world case studies to guarantee that learners obtain both knowledge and practical abilities for conducting web application pentests.
Indeed, networking is the broad term for the process of integrating computers and other devices in order to exchange data and resources. It makes it possible for various devices to communicate
Popular Linux distribution Kali Linux was created especially for penetration testing and digital forensics. Numerous penetration testing tools that are used for network discovery, vulnerability assessment,
The phrase “Python for Hackers” describes the use of the Python programming language to penetration testing, cybersecurity, and hacking. Because of its ease of use, adaptability, and many modules
Of course! The goal of an ethical hacking course is to educate students how to evaluate the security posture of computer networks, applications, and systems in a morally and legally compliant manner.
Often called “ethical hacking,” network penetration testing is the process of mimicking cyberattacks on a network infrastructure in order to find holes and flaws. The objective is to evaluate the network’s
Active Directory penetration testing is typically conducted by experienced cybersecurity professionals using a combination of manual techniques and automated tools.
A web application pentesting course often teaches students how to evaluate the security of online applications for possible flaws and vulnerabilities. This sort of training is useful for security experts,
API Pentesting, also known as Application Programming Interface Pentesting, is the process of examining the security of APIs (Application Programming Interfaces) in order to find and eliminate
Mobile application pentesting, also known as mobile app security testing, is the process of assessing the security posture of mobile applications to identify vulnerabilities and weaknesses that could be exploited by attackers.
Frequently Asked Questions
Several institutes offer Web Security Courses to train students to become professional Web Application Security Experts. However, if you want to rely on the best certification providers for the career-based course, you can get in contact with Cyberon India, which has been offering the Best Web Application Security Course in India for IT Professionals for a long time. This course covers concepts such as
1. Common Security Vulnerabilities,
2. Security Best Practices, and
3. Secure Coding Techniques.
4. Ethical Hacking,
5. Cryptography, and
6. Network Security.
In this process, professionals try to secure web apps from illegitimate access, cyber-attacks, data breaches, and online threats. To protect such apps, one can use the following tools.
1. Authentication,
2. Encryption,
3. Firewalls, and
4. Input Validation.
Moreover, it’s essential to keep your web apps up to date with the latest security updates & regular surveillance for any suspicious activity.
You can follow the below steps to ensure security on a web application:
1. Apply Authentication & Authorization,
2. Use SSL/ TLS,
3. Deploy Encryption,
4. Stricken the Servers security,
5. Validate Input,
6. Surveillance Logs,
7. Utilize Web App Firewalls, and
8. Execute Regular Security Tests.
Following are the Top 10 Web Application Security Risks:
01. SQL Injection,
02. Cross-Site Scripting (XSS),
03. Broken Authentication and Session Management,
04. Insecure Direct Object References,
05. Cross-Site Request Forgery (CSRF),
06. Security Misconfiguration,
07. Unvalidated Redirects and Forwards,
08. Failure to Restrict URL Access,
09. Insufficient Transport Layer Protection, and
10. Using Components with Known Vulnerabilities
Following are the risks associated with web applications that professionals found:
1. Broken Authentication & Session Management,
2. Cross-Site Request Forgery (CSRF),
3. Security Misconfiguration, and
4. Failure to Restrict URL Access
One can see the following security issues in Web Applications:
1. Unvalidated Redirects & Forwards,
2. Insecure Direct Object References,
3. Malicious File Execution, and
4. Insecure Cryptographic Storage
Following are some of the top Security Testing Tools for Web Applications:
01. Acunetix Web Vulnerability Scanner,
02. Burp Suite,
03. Netsparker,
04. Kiuwan,
05. WebInspect,
06. HP WebInspect,
07. IBM AppScan,
08. WAPT Pro,
09. Paros Proxy, and
10. OWASP ZAP
Adversaries use several hacking methods to find loopholes in web apps so that they can exploit them to access the web app’s user control. The end result of which is a confidential data breach. Some of the techniques used to attack web apps are as follows.
1. SQL Injection,
2. Cross-Site Scripting (XSS), and
3. Remote File Inclusion (RFI).
These attacks are purposely executed to steal confidential data, modify websites, and execute more malware attacks.