Mastering API Pentesting: Secure Data Exchange in Modern Applications
- Modules : 10
- Duration: 40 Hours
- Level : Expert
- Rating : ★★★★★
API Pentesting, also known as Application Programming Interface Pentesting, is the process of examining the security of APIs (Application Programming Interfaces) in order to find and eliminate vulnerabilities that attackers may exploit. APIs are critical components of modern software applications, enabling diverse software systems to connect and interact with one another. However, if not adequately protected, APIs can be subject to a variety of attacks, resulting in data breaches, unauthorized access, and other security problems.
API pentesting, also known as Application Programming Interface pentesting, is a specific type of security testing that evaluates the security posture of APIs. APIs are the foundation of modern software systems, allowing communication and data exchange across various applications and services. However, API flaws can disclose sensitive data, jeopardize user privacy, and provide opportunities for attackers to exploit.
API pentesting is a systematic process in which security specialists assess APIs for potential vulnerabilities, flaws, and misconfigurations that hostile actors might exploit. This approach entails simulating attacks on API endpoints to identify security issues and evaluate the efficacy of current security safeguards. The ultimate aim is to detect and mitigate risks in order to protect the confidentiality, integrity, and availability of data transmitted over APIs.
Key Features of API Pentesting:
API Reconnaissance: API Reconnaissance entails understanding the API’s architecture, endpoints, parameters, and functions. This includes identifying all available endpoints and defining what data they receive and return.
Authentication and Authorization Testing: Assessing the efficacy of authentication techniques (e.g., API keys, OAuth tokens) and authorization controls (e.g., role-based access control) to guarantee that only authorized users have access to API services.
Input Validation and Parameter Tampering: Testing for injection vulnerabilities (e.g., SQL injection, XML injection) by modifying input parameters and payloads provided to API endpoints. This helps to identify vulnerabilities that might lead to data tampering or illegal access.
Session Management Testing: Determines how the API handles user sessions and stateful interactions. This covers checking for session fixation, hijacking, and session timeout vulnerabilities.
Error Handling and Exception Management: Examining how the API manages error circumstances and exceptions. Testing for vulnerabilities, such as information leaking, using error messages and stack traces.
Data Integrity and Confidentiality: Ensuring that data transmitted over the API is encrypted in transit (e.g., via HTTPS) and securely stored. This involves scanning for vulnerabilities that might result in data leaking or manipulation.
Rate limitation and Throttling: Determine if the API uses appropriate rate limitation and throttling measures to avoid misuse, DoS (Denial of Service), and brute force assaults.
API Abuse and exploitation: Assessing the API’s resilience against abuse and exploitation. This includes testing for situations in which attackers try to utilize the API for unexpected reasons or execute operations that exceed their allowed rights.
To summarize, API pentesting is an important part of a complete security strategy because it allows companies to proactively find and repair vulnerabilities in their APIs, therefore protecting sensitive data and ensuring the integrity of their systems and applications.
Mastering API Pentesting: Secure Data Exchange in Modern Applications
Course Duration:12 weeks.
Week 1: Introduction to API Security
- Understanding the Role of APIs in Modern Software Development
- An overview of API security concerns and weaknesses.
- Introduction to Common API Attack Vectors
Week 2: API Fundamentals
- Understanding API types (e.g., RESTful, SOAP, and GraphQL)
- Overview of API authentication techniques (API keys, OAuth, and JWT).
- Authorization and access control in APIs
Week 3: API reconnaissance and information gathering.
- Identifying API endpoints, parameters, and functions
- Utilizing tools for API discovery and exploration
- Analyze API documentation and specs.
Week 4: Authentication Test
- Test API authentication techniques for weaknesses (weak credentials, brute force attacks, etc.).
- Exploring OAuth authentication channels and vulnerabilities.
- Evaluating JWT security and best practices.
Week 5: Authorization Testing.
- Testing API authorization controls (role-based access control, scopes, and so on).
- Evaluating permission bypass approaches (horizontal privilege escalation, IDOR).
- Investigating broken access control vulnerabilities in APIs
Week 6: Input Validation and Injection Testing.
- Testing for injection vulnerabilities (such as SQL injection and XML injection)
- Exploring weaknesses in parameter manipulation and input validation.
- Using fuzzing methods to find injection vulnerabilities
Week 7: Session Management and Stateful APIs.
- Evaluating session management strategies in stateful APIs
- Testing for session fixation, hijacking, and session timeout vulnerabilities.
- Exploring state management issues in RESTful APIs.
Week 8: Error Handling and Exception Management.
- Test for security problems in error handling and exception management.
- Analyze error messages and stack traces for information leaks.
- Exploring denial of service (DoS) vulnerabilities using error circumstances.
Week 9 – Data Integrity and Confidentiality
- Evaluating data encryption in transit and at rest.
- Testing for data leaking issues in APIs
- Exploring data integrity and manipulation vulnerabilities
Week 10: Rate Limiting and Throttling.
- Evaluating rate-limiting and throttling methods in APIs
- Exploring DoS and brute-force attacks against APIs
- Test for bypasses and exploitation of rate-limiting restrictions.
Week 11: API Abuse and Misuse.
- Testing for API misuse and abuse scenarios.
- Exploring business logic weaknesses in APIs.
- Evaluate the impact of unsecured direct object references (IDOR) in APIs.
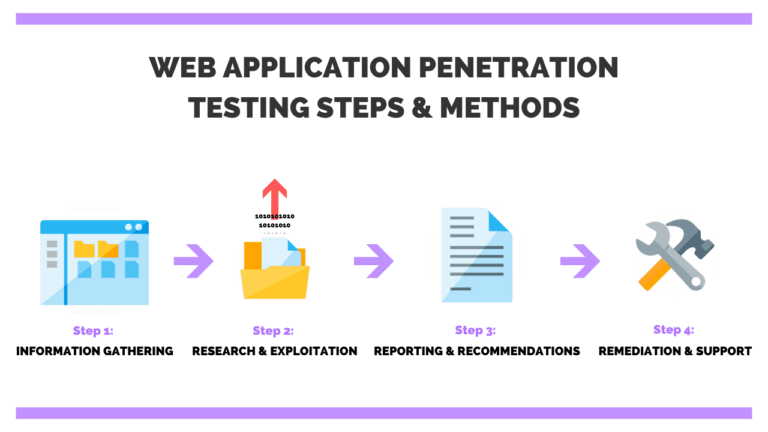
Week 12: Reporting and Remediation
- Generating complete API pentest reports
- Prioritizing vulnerabilities according to risk and effect
- Implementing remedial techniques and safe coding practices
This program offers an organized method to studying API pentesting by covering key concepts, techniques, tools, and legal issues. The course approach combines academic ideas, hands-on laboratories, practical exercises, and real-world case studies to guarantee that learners develop both knowledge and practical skills when conducting API pentests.
Indeed, networking is the broad term for the process of integrating computers and other devices in order to exchange data and resources. It makes it possible for various devices to communicate
Popular Linux distribution Kali Linux was created especially for penetration testing and digital forensics. Numerous penetration testing tools that are used for network discovery, vulnerability assessment,
The phrase “Python for Hackers” describes the use of the Python programming language to penetration testing, cybersecurity, and hacking. Because of its ease of use, adaptability, and many modules
Of course! The goal of an ethical hacking course is to educate students how to evaluate the security posture of computer networks, applications, and systems in a morally and legally compliant manner.
Often called “ethical hacking,” network penetration testing is the process of mimicking cyberattacks on a network infrastructure in order to find holes and flaws. The objective is to evaluate the network’s
Active Directory penetration testing is typically conducted by experienced cybersecurity professionals using a combination of manual techniques and automated tools.
A web application pentesting course often teaches students how to evaluate the security of online applications for possible flaws and vulnerabilities. This sort of training is useful for security experts,
API Pentesting, also known as Application Programming Interface Pentesting, is the process of examining the security of APIs (Application Programming Interfaces) in order to find and eliminate
Mobile application pentesting, also known as mobile app security testing, is the process of assessing the security posture of mobile applications to identify vulnerabilities and weaknesses that could be exploited by attackers.
Frequently Asked Questions
With the increasing reliance on APIs for data exchange in modern applications, they have become a prime target for cyberattacks. Mastering API pentesting is crucial for identifying vulnerabilities and ensuring the security of data transmission, protecting both the organization’s and its users’ sensitive information.
Essential skills include a deep understanding of API technologies and protocols, proficiency in using API testing tools and frameworks, knowledge of common API security vulnerabilities, expertise in manual and automated testing techniques, and the ability to analyze API responses for potential security risks.
Mastering API pentesting is typically considered an advanced career path within cybersecurity. It requires a solid foundation in networking, web application security, and penetration testing principles, as well as specialized knowledge in API-specific security concepts and techniques.
Yes, as more organizations adopt APIs for building and integrating software applications, the demand for professionals skilled in API pentesting is expected to grow. Additionally, with the rise in cyber threats targeting APIs and the increasing emphasis on data privacy and compliance, there will be a continued need for experts capable of securing API-driven ecosystems.
Salaries for professionals with expertise in API pentesting vary depending on factors such as experience, location, industry, and employer. However, according to industry sources, the average salary for professionals in cybersecurity, including API pentesting specialists, ranges from ₹8,00,000 to ₹20,00,000 per year in India.
Organizations across various industries, including technology, finance, healthcare, e-commerce, and government sectors, may hire professionals with expertise in mastering API pentesting. Any organization that relies on APIs for data exchange in their applications and systems would benefit from having API security experts on their cybersecurity team.