“Active Directory Pentesting” refers to a specialized course or training program designed to teach individuals about assessing and securing Active Directory environments from a penetration testing perspective. Active Directory (AD) is a widely used directory service provided by Microsoft, commonly used for managing user identities, resources, and permissions in a networked environment.
In an Active Directory Pentesting course, participants typically learn:
Overview of Active Directory: Understanding the architecture, components, and functionalities of Active Directory.
Pentesting Methodologies: Learning methodologies and techniques for conducting penetration testing specifically targeting Active Directory environments.
Enumeration Techniques: Techniques for discovering and enumerating information about users, groups, computers, and other objects within an Active Directory domain.
Exploitation Techniques: Understanding common vulnerabilities and weaknesses in Active Directory implementations and how to exploit them to gain unauthorized access.
Privilege Escalation: Techniques for escalating privileges within an Active Directory environment, such as abusing misconfigurations or exploiting vulnerabilities.
Persistence: Strategies for maintaining access and persistence within an Active Directory environment after initial compromise.
Post-exploitation Activities: Techniques for gathering sensitive information, lateral movement within the network, and exfiltration of data from an Active Directory environment.
Defense and Mitigation: Strategies and best practices for defending against common Active Directory attacks and mitigating security risks.
These courses are typically aimed at cybersecurity professionals, penetration testers, and IT professionals responsible for securing Active Directory environments. By understanding how attackers target and exploit Active Directory, participants can better defend against these threats and secure their organization’s infrastructure effectively.
Active Directory (AD) is the backbone of many enterprise networks, serving as a centralized system for managing user identities, resources, and permissions. However, its complexity and widespread use make it a prime target for attackers seeking unauthorized access to sensitive information. This course is designed to equip cybersecurity professionals with the knowledge and skills necessary to assess the security of Active Directory environments through penetration testing techniques.
Course Objectives:
- Understand the architecture, components, and functionalities of Active Directory.
- Learn methodologies and tools for conducting effective penetration tests targeting Active Directory environments.
- Discover and enumerate information about users, groups, computers, and other objects within an Active Directory domain.
- Exploit common vulnerabilities and weaknesses in Active Directory implementations to gain unauthorized access.
- Escalate privileges within an Active Directory environment through various techniques.
- Implement strategies for maintaining access and persistence within an Active Directory environment.
- Perform post-exploitation activities, including data exfiltration and lateral movement within the network.
- Understand defensive strategies and best practices for securing Active Directory environments against common attacks.
Course Modules:
- Introduction to Active Directory Security
- Pentesting Methodologies for Active Directory
- Enumeration Techniques
- Exploitation Techniques
- Privilege Escalation
- Persistence Strategies
- Post-exploitation Activities
- Defense and Mitigation Strategies
Course Format:
- Duration: [Number] weeks
- Format: Instructor-led lectures, hands-on labs, demonstrations, and discussions.
- Prerequisites: Basic understanding of networking, cybersecurity concepts, and experience with Windows operating systems.
Who Should Attend:
- Cybersecurity professionals
- Penetration testers
- IT professionals responsible for securing Active Directory environments
Certification: Participants who successfully complete the course and pass the assessment will receive a certificate of completion.
Module 1: Introduction to Active Directory Security
- Overview of Active Directory architecture and components
- Understanding the importance of securing Active Directory environments
- Common security challenges and threats in Active Directory
Module 2: Pentesting Methodologies for Active Directory
- Introduction to penetration testing and its relevance to Active Directory security
- Methodologies for conducting penetration tests in Active Directory environments
- Planning and scoping penetration tests targeting Active Directory
Module 3: Enumeration Techniques
- Techniques for discovering and enumerating information about Active Directory objects
- Enumeration of users, groups, computers, and other objects within an Active Directory domain
- Tools and scripts for automated enumeration
Module 4: Exploitation Techniques
- Common vulnerabilities and weaknesses in Active Directory implementations
- Techniques for exploiting vulnerabilities to gain unauthorized access
- Exploitation of misconfigurations, weak passwords, and insecure group policies
Module 5: Privilege Escalation
- Techniques for escalating privileges within an Active Directory environment
- Exploitation of privilege escalation vulnerabilities
- Abuse of misconfigurations and insecure permissions
Module 6: Persistence Strategies
- Strategies for maintaining access and persistence within an Active Directory environment
- Techniques for backdooring Active Directory objects
- Implementing persistence mechanisms to evade detection
Module 7: Post-exploitation Activities
- Gathering sensitive information from compromised Active Directory environments
- Lateral movement techniques within the network
- Data exfiltration strategies from Active Directory environments
Module 8: Defense and Mitigation Strategies
- Defensive strategies and best practices for securing Active Directory environments
- Hardening Active Directory configurations and implementing security controls
- Detection and response techniques for identifying and mitigating Active Directory attacks
Module 9: Case Studies and Practical Exercises
- Real-world case studies of Active Directory penetration testing scenarios
- Hands-on practical exercises and labs to reinforce concepts learned
- Discussion and analysis of common Active Directory security incidents
Module 10: Final Assessment and Certification
- Final assessment to evaluate understanding of course material
- Certification of completion for participants who successfully pass the assessment
Indeed, networking is the broad term for the process of integrating computers and other devices in order to exchange data and resources. It makes it possible for various devices to communicate
Popular Linux distribution Kali Linux was created especially for penetration testing and digital forensics. Numerous penetration testing tools that are used for network discovery, vulnerability assessment,
The phrase “Python for Hackers” describes the use of the Python programming language to penetration testing, cybersecurity, and hacking. Because of its ease of use, adaptability, and many modules
Of course! The goal of an ethical hacking course is to educate students how to evaluate the security posture of computer networks, applications, and systems in a morally and legally compliant manner.
Often called “ethical hacking,” network penetration testing is the process of mimicking cyberattacks on a network infrastructure in order to find holes and flaws. The objective is to evaluate the network’s
Active Directory penetration testing is typically conducted by experienced cybersecurity professionals using a combination of manual techniques and automated tools.
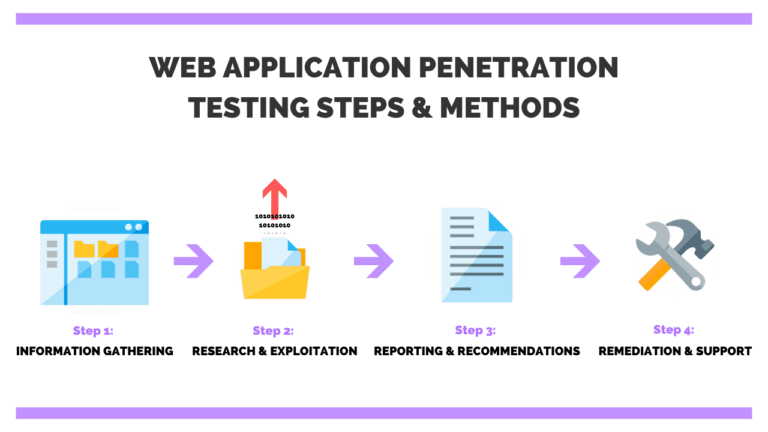
A web application pentesting course often teaches students how to evaluate the security of online applications for possible flaws and vulnerabilities. This sort of training is useful for security experts,
API Pentesting, also known as Application Programming Interface Pentesting, is the process of examining the security of APIs (Application Programming Interfaces) in order to find and eliminate
Mobile application pentesting, also known as mobile app security testing, is the process of assessing the security posture of mobile applications to identify vulnerabilities and weaknesses that could be exploited by attackers.
Frequently Asked Questions
Active Directory serves as a critical component in many organizations’ network infrastructure. Pentesting helps identify vulnerabilities and weaknesses in Active Directory implementations, allowing organizations to proactively secure their systems against potential attacks and unauthorized access.
Essential skills include a deep understanding of Active Directory architecture, penetration testing methodologies, enumeration techniques, exploitation strategies, privilege escalation methods, and post-exploitation activities. Additionally, strong problem-solving, critical thinking, and analytical skills are crucial in this field.
Active Directory Pentesting is typically considered an advanced career path within cybersecurity. It requires a solid foundation in networking, cybersecurity concepts, and hands-on experience in penetration testing or related fields before specializing in Active Directory security.
Yes, as organizations continue to rely on Active Directory for centralized identity and access management, the demand for professionals skilled in securing Active Directory environments is expected to grow. Moreover, with the increasing frequency and sophistication of cyber threats, there is a rising need for specialists capable of conducting thorough penetration tests and securing critical infrastructure.
So, the salary range in INR for Active Directory Pentesting professionals would be approximately ₹60,00,000 to ₹1,12,50,000 per year.