Ethical Hacking: Mastering the Art of Cyber Defense
- Modules : 10
- Duration: 40 Hours
- Level : Expert
- Rating : ★★★★★
Of course! The goal of an ethical hacking course is to educate students how to evaluate the security posture of computer networks, applications, and systems in a morally and legally compliant manner. White-hat hackers, or ethical hackers, utilize their expertise to find holes and flaws in information systems before malevolent intruders can take advantage of them. An overview of what to anticipate from an ethical hacking training is provided below:
In order to find vulnerabilities and flaws, ethical hacking—also referred to as penetration testing or white-hat hacking—involves imitating cyberattacks on computer systems, networks, or applications with the owner’s permission. Ethical hacking is to evaluate an organization’s IT infrastructure’s security posture and assist in strengthening its defenses against malevolent hackers.
The same methods and resources that malevolent hackers use are also used by ethical hackers, but they operate within the law and with the organization’s express consent. They adhere to stringent protocols and moral principles to guarantee that their activities do not impair or interfere with the systems they are evaluating.
Among the fundamental ideas and methods of ethical hacking are:
Assent: Before beginning any testing or evaluation procedures, ethical hackers must have the organization’s express consent.
Legal Compliance: All applicable laws, rules, and industry standards, including the Computer Fraud and Abuse Act (CFAA) in the United States, must be complied with by ethical hacking operations.
Guardianship: All data gathered during testing must be treated as secret by ethical hackers, who should only disclose it to those who have been given permission to do so by the organization.
Reliability: The integrity of the systems being tested must be preserved by ethical hackers, and they must refrain from causing any harm or disturbance.
Expertise: Professional behavior is expected of ethical hackers, and they should properly and concisely convey their findings and suggestions to the company.
Ongoing Education: To make sure they are prepared to evaluate and safeguard IT systems, ethical hackers need to keep up with the most recent security threats, vulnerabilities, and technologies.
Organizations may prevent harmful actors from taking advantage of security vulnerabilities by addressing them early on with the use of ethical hacking. Organizations may improve their defenses and lower the risk of cyberattacks by regularly testing their systems and apps.
Of course! An extensive curriculum overview for the Ethical Hacking course may be found below:
Module 1: Overview of Ethical Hacking
- Recognizing the attitude of ethical hackers
- The fundamentals and techniques of ethical hacking
Ethical and legal aspects
Module 2: Reconnaissance and Footprints
- Information gathering via both active and passive reconnaissance
- Tools and methods for creating footprints
Using publicly available intelligence (OSINT)
Module 3: Counting and Scanning
- Techniques for network scanning (such as ICMP and TCP/UDP scanning)
- Listing services and identifying versions
- searching for vulnerabilities with programs like Nmap and Nessus
Module 4: Evaluation of Vulnerabilities
- Finding and evaluating application, network, and system vulnerabilities
- Database of common vulnerabilities and exposures (CVE)
- Prioritizing and rating vulnerabilities
Module 5: Exploitations
- Taking advantage of weaknesses to get unwanted access
- Frameworks for exploitation (like Metasploit)
- Take advantage of customization and development
Module 6: Sustaining Access and Post-Exploitation
- Use hacked computers to carry out more exploits
- Strategies for elevating privileges
- preserving continuous access and hiding traces
Module 7: Security of Wireless and Networks
- Evaluating the security of wireless networks (WEP, WPA, WPA2)
- Scanning and using wirelessly
- Techniques for mitigating wireless assaults
Module 8: Web application security is covered
- Finding and taking advantage of web application vulnerabilities (such as SQL injection and XSS)
- Techniques for checking web applications for intrusions
- WAFs (web application firewalls) and safe coding techniques
Module 9: Social Engineering
- Social engineering’s psychological foundations
- Typical methods of social engineering (phishing, pretexting, etc.)
- Techniques for preventing social engineering assaults
Section 10: Encryption
- The foundations of cryptography, including digital
- signatures, hashing, and encryption
- Cryptographic algorithms and protocols
- Countermeasures and approaches for cryptanalysis
Chapter 11: Intrusion Detection
- Organizing, carrying out, and documenting penetration testing
- Techniques for penetration testing (e.g., PTES, OWASP)
- Resenting conclusions and suggestions
Module 12: Case Studies and Real-World Applications
- An analysis of real-world cybersecurity case studies
- Using ethical hacking methods to address security issues
- Analysis of current cybersecurity incidents and takeaways
Chapter 13: Final Project
- Create and carry out a thorough penetration test using a mock network environment.
- Compile findings, weaknesses, and suggestions into an expert report.
Extra tools:
- Suggested reading lists, online guides, and tools for learning more
- Availability of online laboratories and training grounds for practical experience
This course offers a methodical evolution in ethical hacking from basic ideas to sophisticated methods. Each module reinforces learning goals and gets students ready for real-world cybersecurity issues with theoretical explanations, practical demonstrations, hands-on laboratories, and case studies.
Indeed, networking is the broad term for the process of integrating computers and other devices in order to exchange data and resources. It makes it possible for various devices to communicate
Popular Linux distribution Kali Linux was created especially for penetration testing and digital forensics. Numerous penetration testing tools that are used for network discovery, vulnerability assessment,
The phrase “Python for Hackers” describes the use of the Python programming language to penetration testing, cybersecurity, and hacking. Because of its ease of use, adaptability, and many modules
Of course! The goal of an ethical hacking course is to educate students how to evaluate the security posture of computer networks, applications, and systems in a morally and legally compliant manner.
Often called “ethical hacking,” network penetration testing is the process of mimicking cyberattacks on a network infrastructure in order to find holes and flaws. The objective is to evaluate the network’s
Active Directory penetration testing is typically conducted by experienced cybersecurity professionals using a combination of manual techniques and automated tools.
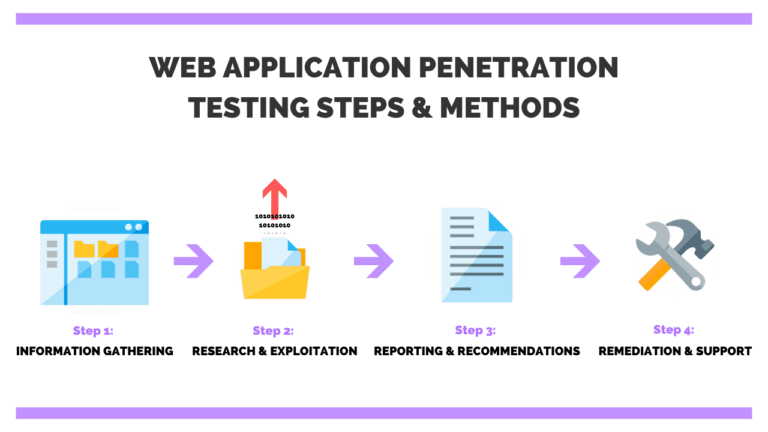
A web application pentesting course often teaches students how to evaluate the security of online applications for possible flaws and vulnerabilities. This sort of training is useful for security experts,
API Pentesting, also known as Application Programming Interface Pentesting, is the process of examining the security of APIs (Application Programming Interfaces) in order to find and eliminate
Mobile application pentesting, also known as mobile app security testing, is the process of assessing the security posture of mobile applications to identify vulnerabilities and weaknesses that could be exploited by attackers.
Frequently Asked Questions
One of the best courses that you can choose to learn ethical hacking is the Certified Ethical Hacker Course offered by Cyberon India. This course is specially designed to introduce students to the fundamental concepts of hacking techniques, & tools used in the process of securing organizational resources.
Concepts such as – encryption, social engineering, pentesting, and many more are introduced in this course for a better understanding of aspirants.
Definitely! Singapore has a high demand for professional ethical hackers to solve cyber security issues for organizations with the latest techniques and tools. So, if you are considering starting your own career in hacking, you can definitely go for ethical hacking.
For that, you can join the Best Ethical Hacking Course in India offered by Cyberon india . This course will help you develop your skills at the level of hacking. The main objective of this course is to train students to become certified hackers who can help organizations to beat online threats that are carrying various threats to the firm and connected partners.
Following are the 3 types of hacking:
1. Black Hat Hacking : In this kind of hacking, the hacker uses various hacking techniques to access a system with an unauthorized connection to steal confidential data.
2. White Hat Hacking : This type of hacking involves legitimate access obtained with lawful hacking techniques with the permission of the owner of the resources. It’s a common practice that comes in proceeding to find security flaws in organizational resources, so one can enhance their security measures before the adversary could hack the systems.
3. Grey Hat Hacking : This type of professional method with an indefinite objective. In this kind of hacking, the hackers find security loopholes and crack them, but they don’t mean harm to anyone.
In India, the average salary for an ethical hacker can range from INR 4 lakh to INR 30 lakh per annum or even higher for experienced professionals or those working in top-tier organizations. The salary may also include additional benefits such as bonuses, incentives, and allowances.
If you want to be a hacker, you can learn about the following things.
1. Computer Science,
2. Cyber Security,
3. Web Development,
4. Programming Language,
5. Networking,
6. Data Analysis,
7. Ethical Hacking
Started the journey of becoming a hacker? Let’s learn things about how to be an ethical hacker. In Singapore, you have various options to become a certified ethical hacker. Some have adopted books to skill up, and some have searched for online material. There some of them have trusted institutes that are offering specially designed courses for the purpose of teaching hacking skills.
You can start your hacking journey by learning a programming language. That’s because you would need the coding ability to put secure codes in the application structure. The easiest computing language that you can start learning is Python.
Now, you can start searching for an ethical hacking course. One of the best options would be the Best Ethical Hacking Course offered by Cyberon India which will help you get introduced to ethical hacking from scratch.
Not a single computing language is specially specified for hacking operations. So, it doesn’t matter which one of the following computing languages you know.
1. Python,
2. JavaScript,
3. C,
4. C++,
5. Ruby,
6. Bash, and
7. SQL
Definitely! For that, you can contact Cyberon India, which offers an Online Ethical Hacking Course, a specially designed course for students outside Singapore. Moreover, you can schedule your sessions at your convenience. What are you waiting for? Contact, Now!
India is experiencing a boom in ethical hacking as a result of the country’s increased emphasis on cybersecurity, expanding digital infrastructure, and the need for qualified experts to protect against online threats.
Because of its technological intricacy, studying ethical hacking might be difficult, but it is possible if you are committed to the subject.
Yes, given the correct tools, direction, and willpower, novices can learn ethical hacking.
In India, ethical hackers make, on average, INR 4 lakh to INR 30 lakh per annum
Yes, knowledge of programming languages is often necessary for ethical hacking since it enables the creation and use of unique tools and scripts for security evaluations.
In India, taking an ethical hacking course might be beneficial since it offers important knowledge and abilities in a subject that is expanding quickly and has a high demand for cybersecurity specialists.
Indeed, given India’s rising reliance on digital infrastructure and the increased threat of cyberattacks, ethical hacking talents are highly sought.
Indeed, ethical hackers work within the law and have permission to carry out security assessments to find and fix flaws.