Comprehensive Network Penetration Testing
- Modules : 10
- Duration: 40 Hours
- Level : Expert
- Rating : ★★★★★
Often called “ethical hacking,” network penetration testing is the process of mimicking cyberattacks on a network infrastructure in order to find holes and flaws. The objective is to evaluate the network’s security posture and assist enterprises in fortifying their defenses against malevolent actors.
An outline of network penetration testing is provided below:
1. Goals:
- Determine weak points: Look for any vulnerabilities in the network infrastructure, such obsolete software, incorrect setups, or unsafe protocols.
- Assess the defenses: Evaluate the performance of security measures including access restrictions, intrusion detection systems, and firewalls.
- Test your ability to respond: Assess the organization’s capacity to recognize, address, and contain security events.
2. Approach:
- Reconnaissance: Acquire knowledge about the target network, including its topology, IP addresses, and domain names.
- Scanning: To find open ports, services, and vulnerabilities on the network, use automated programs.
- Enumeration: Determine which hosts, services, and users are currently active on the network and collect more data to help with the assault.
- Exploitation: Seek to get unauthorized access to the network by trying to take advantage of vulnerabilities found during the scanning and enumeration stages.
- Post-exploitation: Continue to investigate the network, increase privileges, and be persistent after gaining access.
- Reporting: Keep a record of all findings, including systems that were exploited, vulnerabilities that were found, and remedial suggestions.
3. Instruments:
- Vulnerability scanners: Nessus, OpenVAS, and Nexpose are examples of automated technologies that are used to search for known vulnerabilities in systems and network devices.
- Exploitation frameworks: Tools and exploits for assessing network security are gathered by frameworks such as Metasploit.
- Network sniffers: For enumeration and reconnaissance purposes, tools like as Wireshark are used to collect and analyze network data.
- Tools for cracking passwords: Unauthorized access to systems may be obtained by using programs like Hydra and John the Ripper to break passwords.
- Custom tools and scripts: To achieve certain testing goals and scenarios, penetration testers often create their own tools and scripts.
4. Testing Types:
- Black-box testing: Black-box testing involves simulating an external attacker while test personnel are ignorant of the network architecture.
- White-box testing: White-box testing involves simulating an insider threat while having complete knowledge of the network architecture.
- Gray-box testing: Gray-box testing simulates a compromised insider or contractor by having testers with just a limited understanding of the network architecture.
5. Remedial Action and Reporting:
- The penetration tester creates a thorough report detailing the testing results, including systems that were abused, vulnerabilities that were found, and suggestions for fixing them.
- With the help of this report, the company may better prioritize security concerns, fix vulnerabilities, update settings, and enhance security controls.
In general, network penetration testing is an essential part of a company’s cybersecurity plan since it helps find security vulnerabilities and fix them before bad actors can take advantage of them. It helps firms strengthen their entire security posture and provide insightful information on how well security procedures are working.
Network penetration testing, also known as ethical hacking, is a systematic and controlled method for assessing the security of a network infrastructure by simulating cyberattacks. The primary goal of network penetration testing is to detect vulnerabilities and weaknesses in the network before malicious actors exploit them. Here’s a detailed explanation of the procedure:
Pre-engagement Phase:
- During the pre-engagement phase, define the scope and objectives of the penetration test, focusing on the target network, systems, and applications.
- Obtain appropriate authorization and consent from the organization’s stakeholders before conducting the test.
- Gather data about the target network, including IP addresses, domain names, network topology, and technology stack.
Reconnaissance Phase:
- During the reconnaissance phase, passive information gathering is used to gain intelligence about the target network, including public domain information, social media profiles, and network architecture.
- Active reconnaissance involves identifying potential entry points and vulnerabilities using tools such as network scanners, DNS enumeration, and WHOIS lookups.
Scanning and Enumeration Phase:
- During the scanning and enumeration phase, use automated tools such as Nmap, Nessus, or OpenVAS to identify open ports, services, and vulnerabilities on the target network.
- Enumerate active hosts, services, and users to collect additional information for future exploitation.
Vulnerability Analysis and Exploitation Phase:
- The Vulnerability Analysis and Exploitation Phase involves analyzing scanning results to identify potential security vulnerabilities, such as misconfigurations, outdated software, or known exploits.
- Use the identified vulnerabilities to gain unauthorized access to network resources, escalate privileges, or execute arbitrary commands.
- Use penetration testing frameworks such as Metasploit to automate the exploitation process and show the impact of successful attacks.
Post-exploitation Phase:
- In the post-exploitation phase, after gaining access to a system or network segment, conduct additional reconnaissance and lateral movement to explore the environment.
- To ensure continued access to compromised systems, set up backdoors, create user accounts, or install malware.
- Document the techniques and methods used during the post-exploitation phase to demonstrate the potential impact of a successful attack.
Reporting and Remediation Phase:
- Compile a detailed report documenting the findings of the penetration test, including identified vulnerabilities, exploited systems, and recommendations for remediation.
- Present the report to the organization’s stakeholders, including management, IT administrators, and security teams.
- Collaborate with the organization to prioritize and address security issues, patch vulnerabilities, update configurations, and improve security controls to enhance the overall security posture of the network.
Network penetration testing is an essential component of a comprehensive cybersecurity strategy, providing organizations with valuable insights into their security vulnerabilities and helping them proactively identify and mitigate potential risks before they can be exploited by malicious actors.
Of course! The hypothetical Comprehensive Network Penetration Testing and Ethical Hacking course syllabus is provided below in full:
Module 1: Introducing Network Security
1.1 Cybersecurity Overview
- The significance of cybersecurity
- The state of cybersecurity today
- And the main cyberthreats
1.2 Foundations of Ethical Hacking
- What ethical hacking is and why it’s done
- How to distinguish it from malicious hacking
- How ethical hacking fits into cybersecurity
1.3 Ethical and Legal Aspects to Consider
- Rules and legislation controlling ethical hacking
- Moral principles and professional behavior
- Accountability and obligations
Module 2: Foundations of Networking
2.1 Concepts of TCP/IP
- Being familiar with the TCP/IP protocol family
- Every layer’s functionality; every layer’s common protocols
2.2 Network Architecture and OSI Model
- An overview of the OSI model
- The function of each OSI layer
- The elements and relationships of network architecture
2.3 Roles of Network Components
- The purposes of switches, routers, and firewalls
- Network hardware, including configurations
- Segmenting networks and their significance
Module 3: Methods of Penetration Testing
3.1 Overview of Intrusion Testing
- Penetration testing methods (e.g., OWASP, PTES) – The goal and extent of penetration testing
- The significance of a methodical approach
3.2 Information Collection and Reconnaissance
- Strategies for both active and passive scouting
- Information collecting tools (such as WHOIS and DNS searches)
- Making a profile with information
3.3 Enumeration and Scanning of Networks
- Network scanning techniques (e.g., Nmap)
- Methods of enumeration, such as SNMP enumeration
- Determining active hosts and accessible ports
Module 4: Instruments and Methods
4.1 Overview of Tools for Penetration Testing
- Nmap, Metasploit, Wireshark, Burp Suite, and further
- Tools for penetration testing selection criteria
- Constructing an environment for penetration testing
4.2 Practical Activities
- Using tools practically in simulated situations
- Basic exploitation, enumeration, and scanning exercises
- Resolving typical problems
Module 5: Vulnerability Assessment
5.1 Finding the Weaknesses
- Frequent network vulnerabilities
- Vulnerability databases and resources
- The significance of evaluating vulnerabilities
5.2 Tools for Vulnerability Scanning
- Overview of technologies like OpenVAS and Nessus
- Setting up and executing vulnerability assessments
- Examining scan outcomes
Module 6: Exploitation Techniques
6.1 Typical Points of Attack
- Taking advantage of security holes in networks
- Social engineering assaults
- Distributing malware and payloads
6.2 Real-World Exploitation Exercises
- Interactive laboratories showcasing exploitation strategies
- Simulated situations to gain real-world experience
- Examining the effects of exploits that are successful
Module 7: Post-Exploitation
7.1 Sustaining Entry
- Persistent access methods
- Avoiding detection
- Tracking hacked systems
7.2 Privilege Escalation
- Finding and taking use of vulnerabilities related to privilege escalation
- Methods for raising privileges on a compromised system
Module 8: Wireless Network Security
8.1 Evaluating Wi-Fi Networks
- Recognizing wireless encryption and weaknesses
- Being familiar with wireless security protocols (WEP, WPA, and WPA2)
- Making evaluations of wireless networks
8.2 Interactive Labs on Wireless Security
- Wireless network security
- Wireless password cracking
- Rogue wireless device detection
Module 9: Web Application Security
9.1 Web Application Security Fundamentals
- Typical vulnerabilities in web applications (such as SQL injection and XSS)
- Web development security recommended practices
- An overview of web application firewalls (WAFs)
- Web application security testing tools
9.2 Testing and Securing Web Applications
- practical activities for locating and taking advantage of web
- vulnerabilities Applying safe coding techniques
Module 10: Reporting and Documentation
10.1 Producing Detailed Reports
- The format of a penetration testing report
- A succinct and clear explanation of the results
- Remedial suggestions
10.2 Communication with Stakeholders
- Addressing queries and concerns
- Skillfully conveying technical results to stakeholders that lack technical expertise
- Working together to solve problems
Module 11: Ethical and Legal Aspects
11.1 Legal Framework for Ethical Hacking
- National and international legislation that are pertinent to ethical hacking
- Case studies and prior legal decisions
- Legal ramifications of unauthorized access
1.2 Ethical Guidelines and Compliance
- Penetration tester compliance requirements
- Professional associations and ethical standards
- Making moral decisions in cybersecurity
Module 12: Complex Subjects
12.1 Complex Methods of Exploitation
- Zero-day exploits and vulnerabilities
- APTs, or advanced persistent threats
- Creating and tailoring exploits
2.2 Red Teaming Exercises and Simulations
- Organizing and carrying out red team operations
- Modeling cyberattacks
- Gaining knowledge from red teaming encounters
The goal of this program is to give students a thorough understanding of ethical hacking and network penetration testing. Through interactive labs and useful exercises, it emphasizes real-world application while covering fundamental concepts, tools, and procedures.
Indeed, networking is the broad term for the process of integrating computers and other devices in order to exchange data and resources. It makes it possible for various devices to communicate
Popular Linux distribution Kali Linux was created especially for penetration testing and digital forensics. Numerous penetration testing tools that are used for network discovery, vulnerability assessment,
The phrase “Python for Hackers” describes the use of the Python programming language to penetration testing, cybersecurity, and hacking. Because of its ease of use, adaptability, and many modules
Of course! The goal of an ethical hacking course is to educate students how to evaluate the security posture of computer networks, applications, and systems in a morally and legally compliant manner.
Often called “ethical hacking,” network penetration testing is the process of mimicking cyberattacks on a network infrastructure in order to find holes and flaws. The objective is to evaluate the network’s
Active Directory penetration testing is typically conducted by experienced cybersecurity professionals using a combination of manual techniques and automated tools.
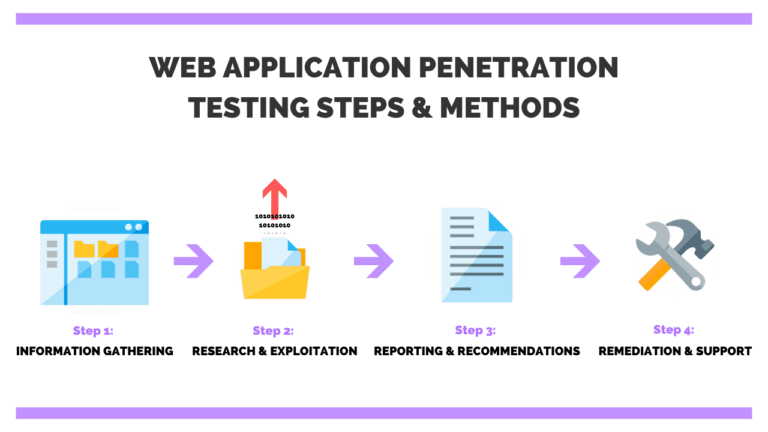
A web application pentesting course often teaches students how to evaluate the security of online applications for possible flaws and vulnerabilities. This sort of training is useful for security experts,
API Pentesting, also known as Application Programming Interface Pentesting, is the process of examining the security of APIs (Application Programming Interfaces) in order to find and eliminate
Mobile application pentesting, also known as mobile app security testing, is the process of assessing the security posture of mobile applications to identify vulnerabilities and weaknesses that could be exploited by attackers.