Indeed, networking is the broad term for the process of integrating computers and other devices in order to exchange data and resources. It makes it possible for various devices to communicate with one another, sharing information and working together. There are many different tools and techniques for networking, such as:
- A local area network (LAN): A local area network links devices in a constrained space, such a house, workplace, or educational institution. Wi-Fi and Ethernet cables are frequently used to create LAN connections.
- Wide Area Network (WAN): A WAN connects local area networks (LANs) over long distances by spanning a broader geographic region. The largest WAN is the internet, although private WANs may also be established with the use of MPLS, VPNs, and leased lines.
- Wireless networking: Technologies such as Bluetooth, Wi-Fi, and cellular networks enable device communication without the need for physical cords.
- A local area network (LAN): A local area network connects devices within a limited area, such a home, office, or school. Ethernet cables and Wi-Fi are widely utilized to establish LAN connections.
- Networking Devices: Common networking devices that aid in facilitating communication between devices on a network include routers, switches, hubs, and access points.
- Network security: Network security is the process of shielding networks against online threats, illegal access, and data breaches. Intrusion detection systems (IDS), firewalls, encryption, and antivirus software are some of the techniques used.
- Cloud Networking: Cloud networking is the process of creating and managing networks with the use of cloud computing resources. In contrast to conventional networking techniques, it provides cost-effectiveness, scalability, and flexibility.
- Peer-to-peer networking: This type of networking allows devices to speak with one another directly rather than through a centralized server. This method is frequently found in file-sharing software.
A key component of contemporary computing is networking, which makes it possible to do everything from simple web surfing to intricate corporate processes. IT specialists, system administrators, and everyone else dealing with computers and technology need to understand networking fundamentals.
The process of joining computers, gadgets, and systems to facilitate resource sharing, cooperation, and communication is known as networking. It includes a broad spectrum of technologies, protocols, and approaches designed to make it easier for devices that are linked to exchange information and services.
Fundamentally, networking is the process of connecting things, either wirelessly using radio waves or physically via wires. Devices can send and receive data packets over these connections, facilitating the sharing of information and the performance of several activities.
Important elements of networking consist of:
Hardware
- Networking hardware consists of cables, network interface cards (NICs), hubs, access points, switches, routers, and modems. These gadgets are in charge of making data transfer throughout the network easier.
Network protocols
- These are collections of guidelines that control data flow over a network. DNS (Domain Name System), HTTP (Hypertext Transfer Protocol), FTP (File Transfer Protocol), and TCP/IP (Transmission Control Protocol/Internet Protocol) are a few examples.
Networking Topologies
- A network’s logical or physical architecture is determined by its topology. There are several common topologies, each having pros and cons for fault tolerance, scalability, performance, and ring, mesh, and hybrid configurations.
Network Security
- To safeguard data and resources from malicious assaults, illegal access, and interception, network security measures are crucial. Networks are protected from cyber attacks by security methods such intrusion detection systems (IDS), firewalls, encryption, and authentication.
Network Services
- These services give users and apps access to a range of features and resources, including as web hosting, email, file sharing, printing, remote access, and video conferencing. Networked devices and equipment are usually used to access these services.
Of course! A course’s curriculum is the detailed plan or overview of the subjects, exercises, quizzes, and materials that comprise the course’s instructional content and framework. It acts as a roadmap for teachers to efficiently plan and deliver lessons, and it helps students comprehend the material they will be covering over the course of the semester.
The following essential elements are frequently seen in a course curriculum:
1. Course Title and Description
- A concise summary of the course’s content, goals, and objectives should be included in the title, which should accurately reflect the course’s subject matter.
2. Learning Outcomes/Objectives
- Clearly defined objectives that specify what knowledge, skills, or abilities students should possess at the conclusion of the course. Assessment and instructional design are guided by learning outcomes.
3. Course Outline/Syllabus
- An in-depth analysis, usually in chronological order, of the subjects, concepts, or units covered in the course. Information on readings, assignments, tests, and grading standards may be included in the syllabus.
4. Instructional Methods & Strategies
- An explanation of the methods, exercises, and approaches to teaching that will be employed to support learning. Lectures, conversations, group projects, practical exercises, role-playing, multimedia presentations, and more may be a part of this.
5. Assessment & Evaluation
- A description of the methods used to gauge and analyze students’ learning throughout the course of the semester. This might contain details on participation, grading guidelines, papers, projects, quizzes, exams, and presentations.
6. Resources and Materials:
- A list of compulsory or suggested readings, software, lab equipment, textbooks, and other materials that complement learning objectives and activities is included in the resources and materials section.
7. Timetable or schedule
- That details the dates and times of particular topics, assignments, tests, and other course-related activities. It assists students in efficiently organizing their time and studying.
8. Policies and Expectations
- Details on expectations for the course, academic integrity, attendance requirements, communication procedures, and other significant administrative information.
9. Support and Accessibility
- Directions for obtaining the resources, accommodations, and support services that are available to students who might need help because of a disability, a language barrier, or other circumstances.
10. Course Evaluation and Revision
- Arrangements for gathering input from participants and students in order to assess the course’s efficacy and refine it for next versions.
All things considered, a well-crafted course curriculum offers a disciplined framework that both teachers and students may work within to meet learning goals and successfully complete educational objectives. It provides direction for the process of teaching and learning and enhances the general caliber and consistency of the educational
Indeed, networking is the broad term for the process of integrating computers and other devices in order to exchange data and resources. It makes it possible for various devices to communicate
Popular Linux distribution Kali Linux was created especially for penetration testing and digital forensics. Numerous penetration testing tools that are used for network discovery, vulnerability assessment,
The phrase “Python for Hackers” describes the use of the Python programming language to penetration testing, cybersecurity, and hacking. Because of its ease of use, adaptability, and many modules
Of course! The goal of an ethical hacking course is to educate students how to evaluate the security posture of computer networks, applications, and systems in a morally and legally compliant manner.
Often called “ethical hacking,” network penetration testing is the process of mimicking cyberattacks on a network infrastructure in order to find holes and flaws. The objective is to evaluate the network’s
Active Directory penetration testing is typically conducted by experienced cybersecurity professionals using a combination of manual techniques and automated tools.
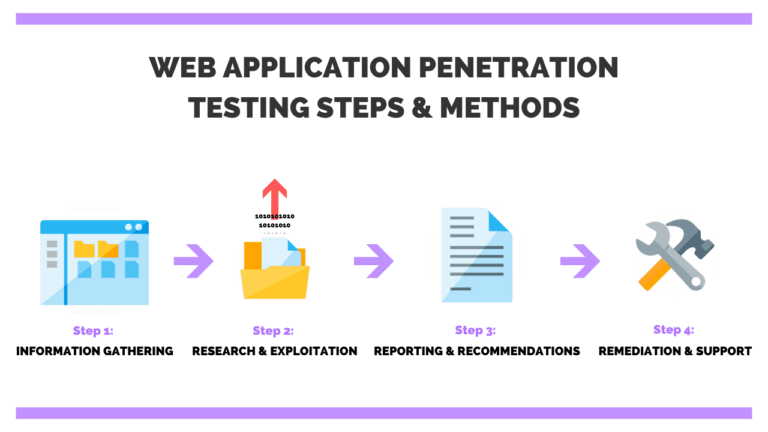
A web application pentesting course often teaches students how to evaluate the security of online applications for possible flaws and vulnerabilities. This sort of training is useful for security experts,
API Pentesting, also known as Application Programming Interface Pentesting, is the process of examining the security of APIs (Application Programming Interfaces) in order to find and eliminate
Mobile application pentesting, also known as mobile app security testing, is the process of assessing the security posture of mobile applications to identify vulnerabilities and weaknesses that could be exploited by attackers.
Frequently Asked Questions
If you want to join the best course for networking as a beginner, you can join the Basic Networking Course in India 2023, offered by Cyberon India. This course will introduce networking concepts for IT Professionals with the latest techniques and tools going to be used in the protection of networks from unauthorized access/ online threats.
This certificate is valid in various countries, so you don’t need to worry about job placements anymore. What are you waiting for? Contact, Now!
You can follow the following steps to become a non-experienced network engineer.
1. You should start learning about networking from various sources, such as online courses, seminars, and certifications available in the Industry.
2. Once got certified with the certification, build a portfolio of your work experience. In your portfolio, things as follows should be mentioned.
a. Project Completed,
b. Certifications, and
c. Other Skillsets.
1. Start collaborating with networking groups, attend industry events, and connect with networking professionals to gain more knowledge.
2. Then, you can start working as an intern in any company offering networking job placements.
3. Gain experience and apply for the expected job profiles.
Of Course, Networking skills are in high demand. As organizations increase the use of digital networks to perform daily tasks on online stores & databases, the demand for networking skills rises with it.
Organizations need such skills for designing, managing, and maintaining networks with utmost security & efficiency.
There are no prerequisites for joining the Basic Networking Course in Singapore 2023. Anyone who has a keen interest in learning skills & knowledge related to networking can go for this course by contacting Cyberon India.
IT Professionals & Networking Administrators who want to enhance their skills in networking. However, if you have a basic understanding of PC & networks, learning networking concepts would be easy.
If you want to become a networking professional and want to rely on a reliable network, you can contact CYBERON India, which has been offering the Best Basic Networking Course in India 2023 for IT Aspirants.
Under professional networking experts, you’ll be able to follow your career path with ease. What are you waiting for? Contact, Now!
There is no definite answer to this question. That’s because it depends on the individual’s skills & qualifications. In countries where tech industries have a strong foot in the market, they will have more networking job opportunities for professionals.
Such countries include – the United States, Canada, the United Kingdom, and Singapore. However, countries growing alongside, such as India, would be a great option for networking jobs.
For that, you can start learning several topics, such as
1. Computer Networking,
2. Network Architecture,
3. Routing Protocols,
4. Network Security,
5. Virtualization,
6. Switching,
7. Firewalls, and
8. Cloud Computing.
Or you can join the Basic Networking Course in Singapore 2023 offered by Craw Singapore. This course will introduce you to networking fundamentals with the topics such as
1. Network & Systems Administration,
2. Network Design & Installation,
3. Troubleshooting & Problem Solving, and
There are several things that you can do after completing the networking course. You can go for advanced networking courses to skill up in the networking field. This will give you exposure to how professionals work in the networking sector with the latest techniques and tools to secure networks from online threats.
This will help you to get more skilled and let you several opportunities of getting job placements at high salary packages. Joining a company as an intern would be a great option. You can apply for job profiles, such as
1. Network Engineer,
2. Security Analyst, or
3. System Administrator.